Five Key Features of Portainer
Five Key Features of Portainer 1. Docker Environments 2. Access Control 3. CI/CD Capabilities 4. …


In the digitally connected world, constantly logging into various services is more than just a nuisance—it’s a challenge for data security and user experience. An advanced solution to this dilemma is Single Sign-On technology (SSO). It allows users to log in once and gain access to multiple services without needing to enter separate credentials for each service.
However, behind SSO are various protocols and technologies responsible for its seamless operation. In this post, we will take a closer look at these technologies, particularly OAuth, OpenID, SAML, and SCIM. These concepts play a central role in the implementation and management of Single Sign-On solutions.
The purpose of this article is to provide a comprehensive overview of the mentioned technologies and to present their respective use cases, benefits, and challenges. By the end of this post, you will be able to make informed decisions about which technologies are best suited for your specific needs.
<div class="text-sm leading-relaxed text-gray-700 dark:text-gray-300">
It is advisable to make appropriate data backups before making significant changes to existing systems. Please note that further individual adjustments may be necessary depending on your specific configuration.
</div>
</div>
The idea behind Single Sign-On (SSO) is simple yet effective: A user logs in once to a service and gains access to a multitude of applications and platforms. This eliminates the need to store and enter separate usernames and passwords for each service.
In companies and organizations where dozens or even hundreds of applications are in use, SSO can not only significantly enhance user-friendliness but also improve security. By reducing the number of required passwords, the risk of using weak or repeated passwords is minimized. Additionally, SSO enables centralized control of user access, simplifying the management of permissions and monitoring of security policies.
<div class="text-sm leading-relaxed text-gray-700 dark:text-gray-300">
Despite the obvious benefits, SSO is not a one-size-fits-all solution. In certain cases, such as particularly sensitive applications, multi-factor authentication or even separate logins may be advisable.
</div>
</div>
OAuth, short for “Open Authorization”, acts as a kind of doorman in the digital space. It provides a secure way for applications to access information and resources without the user having to share their login credentials directly with the application. Think of OAuth like a hotel key that gives you access to certain rooms (resources) but not the entire building (all your data).
The flexibility of OAuth makes it an ideal choice for various types of applications, from social networks to professional services. It is often used as a bridge between different services, creating an efficient and secure user experience. OAuth allows you to avoid logging in separately for each service, thus simplifying the login process significantly. It also offers robust security features that benefit both service providers and end users.
OpenID Connect is an extension of OAuth and serves not only for authentication but also for identity verification. It allows users to log in to various services with a single identity without needing separate credentials for each service. Think of it as a universal key for the internet.
OpenID Connect minimizes the need to manage multiple usernames and passwords and provides a consistent solution for identity verification. It allows you to use already validated information from your OpenID Connect provider, reducing, for example, phishing risks, as credentials are only shared with verified and trusted services. OpenID Connect is thus ideal for users looking for a consistent digital identity and for service providers wanting to offer a fast, secure, and modern login option.
SAML (Security Assertion Markup Language) is an XML-based framework frequently used in the corporate world for authentication and authorization processes. It is particularly effective for access management in large organizations using multiple applications and services.
With SAML, companies can implement a single sign-on solution across multiple applications and services. This simplifies management and increases security, as fewer credentials need to be stored and retrieved. It also offers increased control over access rights, which is particularly beneficial when integrating third-party applications or cloud services. By standardizing authentication data, the attack surface for potential security breaches is reduced, as fewer manual interventions are required.
SCIM (System for Cross-domain Identity Management) is an open standard that enables the automation of identity management across different platforms and services. It acts like a universal translator for user data between different systems.
SCIM provides a standardized way to synchronize user data between different systems. This facilitates the integration of new applications and services without requiring manual data migration. Administrators can efficiently manage user accounts, saving time and resources. Additionally, SCIM enables a faster onboarding experience for new employees and reduces the complexity of managing access rights. The standardized data flow enhances data security and minimizes error sources that could result from manual processes.
The choice between OAuth, OpenID, SAML, and SCIM depends on the specific requirements and context in which the technology is used. OAuth and OpenID are particularly suitable for consumer applications and web services where user-friendliness is more important than complex access rights. SAML is the better choice for enterprise environments with high security requirements and complex access models. SCIM is especially useful for managing user identities across different systems, often combined with SAML or OAuth/OpenID for a complete identity and access management solution.
In general, linking the various concepts can create synergies. For example, OpenID can work as an identity provider over OAuth, and SCIM can be integrated with SAML to create a more robust authentication and authorization structure. This way, companies can achieve a high level of flexibility and adaptability to meet specific requirements and challenges.
Single Sign-On (SSO) is more than just a “nice-to-have” today; it is an indispensable tool for any modern company using a variety of applications and services. The benefits are undeniable: increased security, simplified access management, and a better user experience. The question should not be whether to implement SSO but rather which of the presented concepts—OAuth, OpenID, SAML, or SCIM—best fits your needs.
Depending on company size, security requirements, and specific needs, a combination of these technologies may be the best solution. But what if you are looking for an all-in-one solution that unites all these concepts in a seamless experience? Then Authentik comes into play.
Authentik offers exactly what the individual concepts provide and even goes a step further. It is a comprehensive tool that bundles OAuth, OpenID Connect, SAML, and SCIM into a single platform. The goal? To reduce complexity and make the authentication process as seamless as possible.
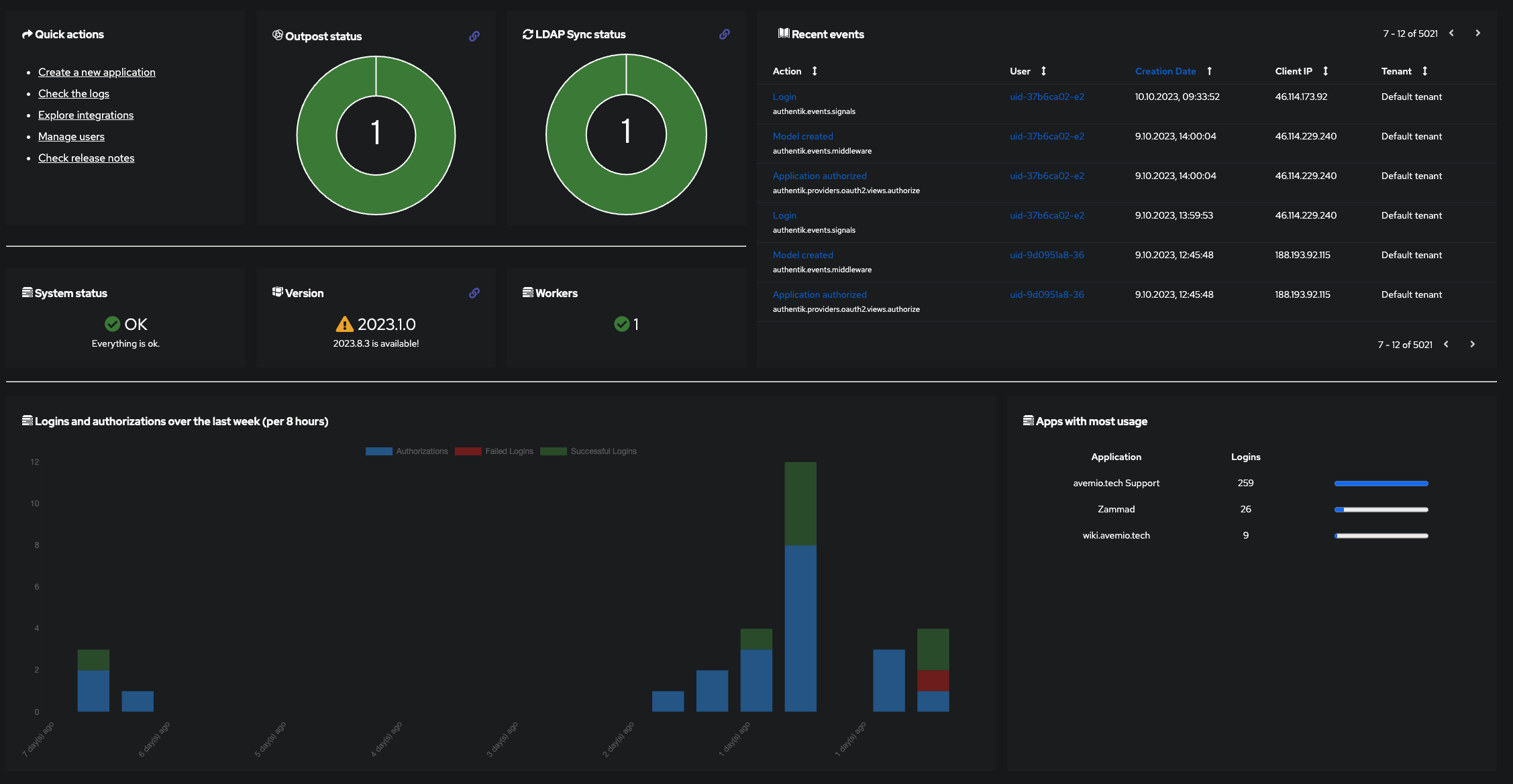
Think of Authentik as your personal identity orchestrator. It ensures that all elements of your authentication system—from Single Sign-On to advanced enterprise solutions—operate in harmonious coexistence. But Authentik goes beyond mere integration. It offers detailed insights into user activities, access levels, and permissions and allows for detailed control over who can access what.
The benefits are manifold. On one hand, the user experience is significantly improved; the need to remember multiple passwords is eliminated. On the other hand, you enhance the security of your system as Authentik allows you to precisely control which services can be used with which credentials. Finally, it offers companies the flexibility to manage various authentication systems in a unified interface, greatly simplifying system maintenance and updates.
By integrating multiple authentication protocols and standards into one platform, Authentik can serve as a one-stop solution for companies of all sizes and industries. Whether you are just starting with digitalization or a large enterprise with complex authentication requirements, Authentik offers a scalable, secure, and user-friendly solution that grows with your needs.
<div class="text-sm leading-relaxed text-gray-700 dark:text-gray-300">
Interested? We are happy to provide you with a highly available instance of <a href="/cloud/kubernetes/apps/authentik/">Authentik</a>. You just need to secure your end systems, and we’ll take care of the rest!
</div>
</div>
Five Key Features of Portainer 1. Docker Environments 2. Access Control 3. CI/CD Capabilities 4. …
Why This Post? What is Portainer? Practical Section Deploying Portainer Setting Up Portainer …
Kubernetes can help a software or digitalization agency generate additional revenue through the …