Immutable Releases on GitHub – A Significant Milestone for a Secure Software Supply Chain
The security of the software supply chain is one of the central topics in modern software …
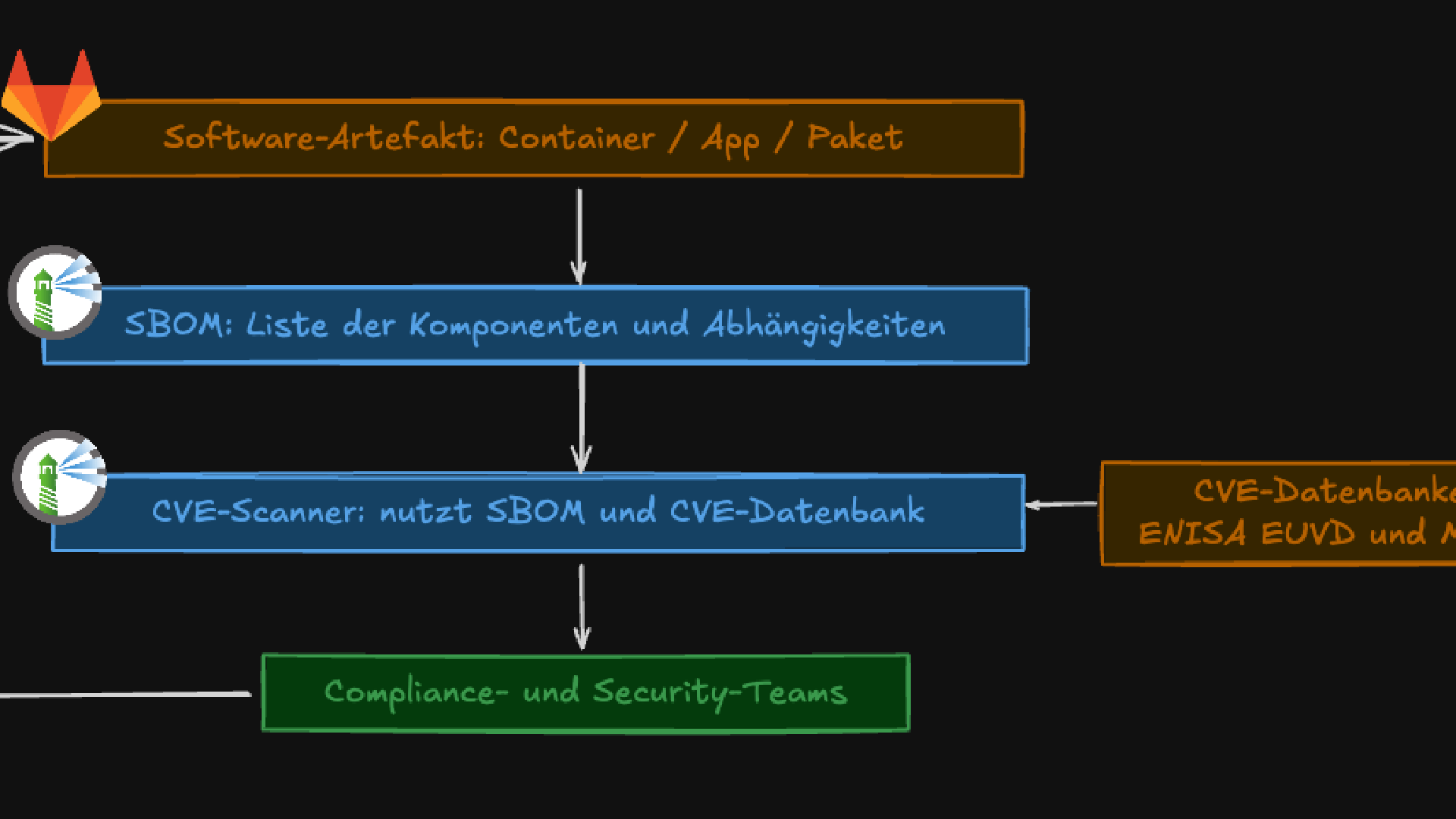
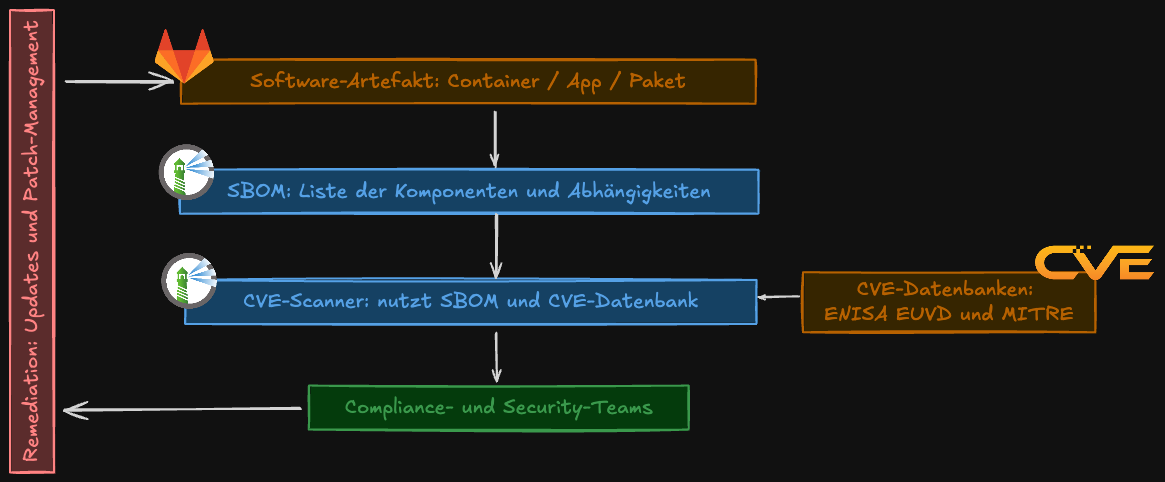
The security of software supply chains is one of the central topics in IT security today. Companies are under increasing pressure to ensure transparency, traceability, and reliability of the software they use. A key tool in this regard is the Software Bill of Materials (SBOM), complemented by automated scanning for known vulnerabilities – Common Vulnerabilities and Exposures (CVE).
In this post, we will:
A Software Bill of Materials is essentially a bill of materials for software. It describes the components that make up software – similar to the bills of materials used in industrial manufacturing.
Let’s imagine a modern car. A car manufacturer knows exactly:
This exact concept is applied to software with an SBOM:
The SBOM is thus a kind of “digital twin” of a software supply chain – it makes visible which components are in use.
There are various standards that have been established internationally:
Each of these standards aims to describe software components in a machine-readable, interoperable, and unambiguous way.
While SBOMs provide the inventory, a system is needed to associate known vulnerabilities with the respective components. This is where Common Vulnerabilities and Exposures (CVE) come into play.
CVE is a list of known security vulnerabilities and exposures that serves as a global reference. Each vulnerability is assigned a unique identifier, e.g.:
The two most important “sources of truth” are:
Both data sources are the foundation for almost all automated security tools.
With an SBOM, it is possible to automatically check for each library used:
Without CVEs, SBOMs would be worthless because they would only represent a list. Only by matching with CVE databases does real value emerge.
The combination of SBOM and CVE scanning is the central building block of a secure software supply chain.
When the Log4Shell vulnerability (CVE-2021-44228) became known in December 2021, thousands of companies worldwide faced the challenge: Where do we use Log4j?
The SBOM is thus the foundation, CVE databases provide the attack vectors – and together they enable quick and targeted action.
GitLab offers extensive security features directly in CI/CD pipelines:
Harbor is an open-source registry for container images:
By integrating these tools into CI/CD pipelines, security becomes a continuous process rather than a downstream check.
For many companies, SBOM and CVE scanning are not only a matter of security but also of compliance.
Compliance teams thus benefit massively from automation.
The discussion about secure software supply chains has shown through incidents like Log4j or the Bitnami incident how vulnerable global ecosystems are. With SBOM and CVE scanning, we have tools at our disposal to significantly reduce these risks.
For companies – especially in regulated industries – the introduction of such processes is no longer a “nice-to-have” but an essential requirement for security, compliance, and resilience.
The security of the software supply chain is one of the central topics in modern software …
Since September 8th, concrete evidence has emerged that a number of extremely widespread NPM …
Kubernetes has become the de facto standard for operating cloud-native applications. However, with …