Immutable Releases on GitHub – A Significant Milestone for a Secure Software Supply Chain
The security of the software supply chain is one of the central topics in modern software …
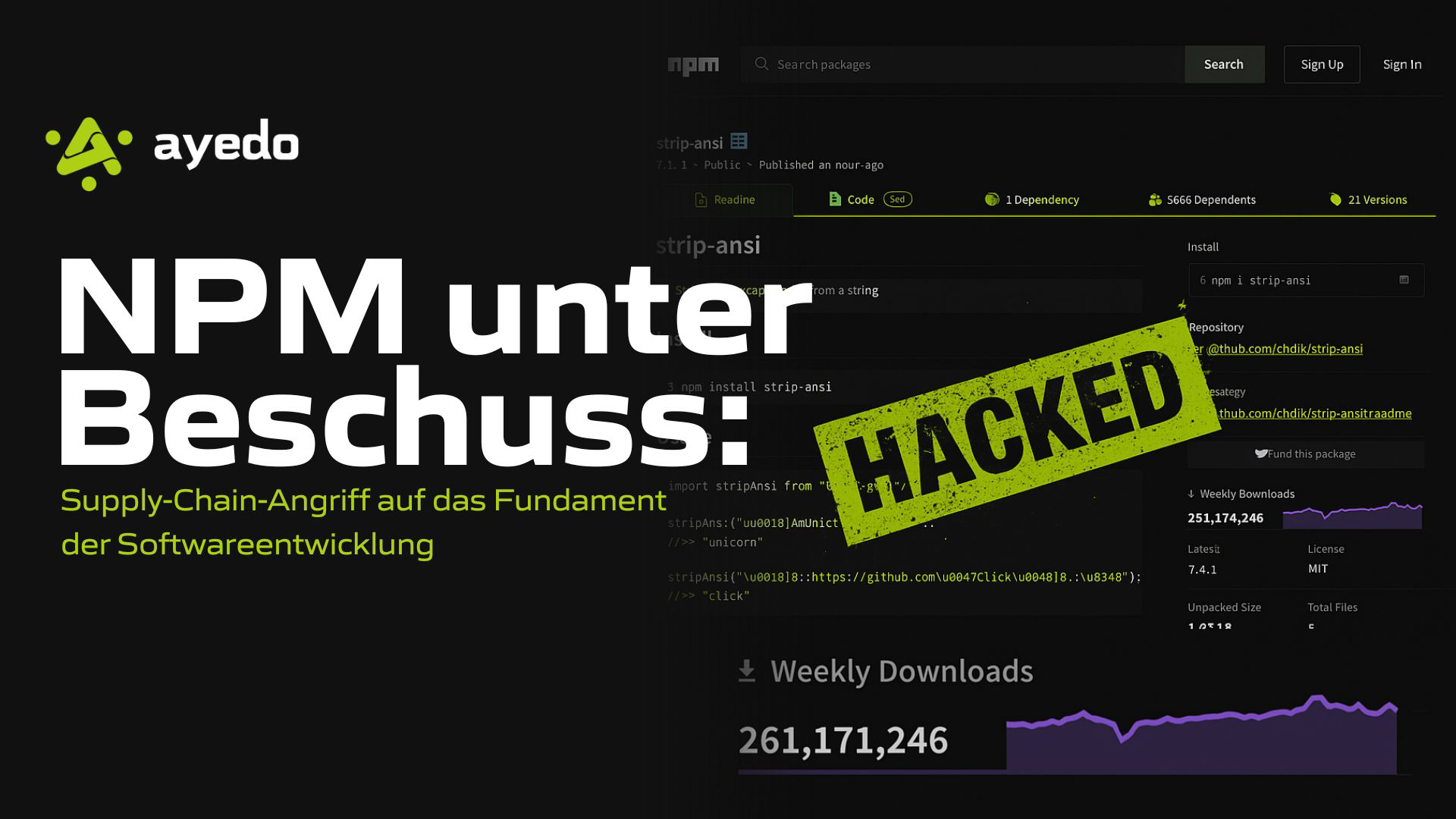
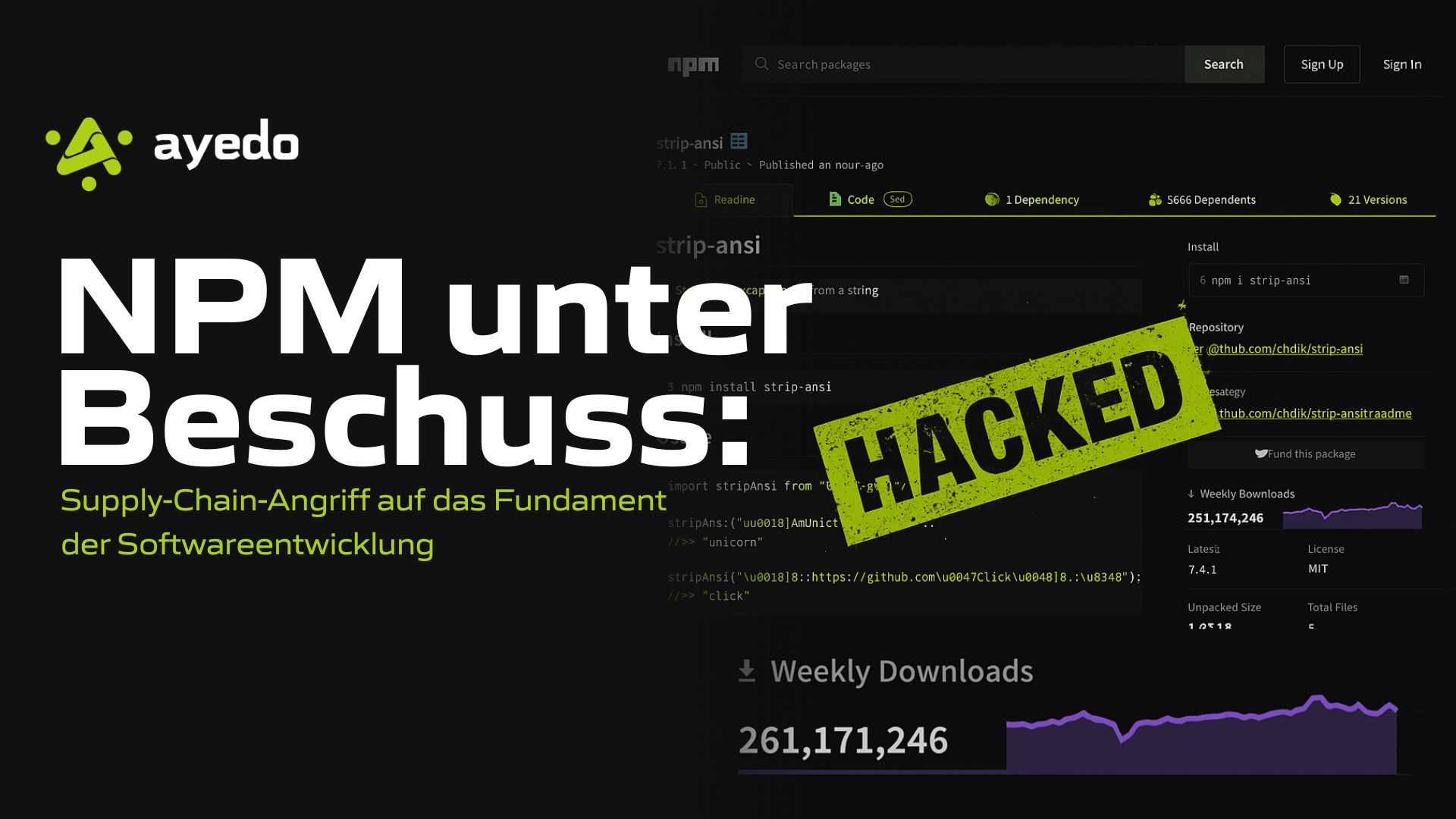
Since September 8th, concrete evidence has emerged that a number of extremely widespread NPM packages — including debug, chalk, ansi-styles, supports-color, and other core components of the Node.js ecosystem — have been compromised. According to public accounts, the maintainer was tricked via phishing into a fake NPM support domain, leading to the release of new, tampered versions that, in total, are downloaded billions of times weekly across the entire set, potentially infiltrating virtually every modern frontend, backend, and CI/CD pipeline.
Those who consider this “just an open-source problem” misunderstand the operational reality: NPM is the world’s largest package registry, operated by Microsoft in the GitHub context, thus a de facto single point of failure for the JavaScript world. “A harmless minor update” in a transitive dependency is often an automated production change today — because pipelines run at night, caches are invalidated in the morning, and deployments proceed without manual gatekeepers, which boosts productivity while maximizing the attack surface.
The injected versions contain obfuscated browser code that hooks into the runtime early: fetch and XMLHttpRequest are “wrapped,” wallet APIs like window.ethereum (EVM) and common Solana interfaces are hooked, responses and requests are altered on-the-fly, and address patterns for Ethereum, Bitcoin (Legacy/SegWit), Solana, Tron, Litecoin, and Bitcoin Cash are detected to replace legitimate target addresses with deceptively similar, attacker-controlled destinations. Additionally, in EVM transactions, the to-address is rewritten or the allowance recipient is manipulated during approve calls, so even if the UI seems “correct,” the signed transaction releases funds to third parties. In short, it’s a multi-layered man-in-the-app approach that intercepts both network layers and application APIs — and can cause real damage in test environments once real wallets are involved.
The affected libraries are basic components (logging, ANSI handling, color and string utilities) embedded in countless toolchains; they enter build scripts, CLI tools, SSR stacks, edge functions, and frontends as transitive dependencies, automatically, cached, and often “hands-free.” This means: Even if your product has no Web3 functionality, the compromised code can run in browser contexts (e.g., developer tools, internal portals, or admin frontends) — rewriting network calls, leaking session contexts, or simply undermining integrity guarantees.
The hard truth is: As long as deployments resolve directly against public registries, your release process is only as secure as the weakest dependency of the weakest maintainer.
Supply chain security is not a tool purchase but an operational duty: It requires clearly assigned responsibility (AppSec/Platform), binding policies (when a new version may enter staging/prod), automated enforcers (pipelines, admission controllers, proxy policies), and playbooks for emergencies (blocking, downgrades, token rotation, customer communication). Without this groundwork, every “ad-hoc reaction” ends in a blind flight — and blind flight in supply chain attacks equals loss of trust.
Anyone responding with “We have no budget” confuses cost with risk: You’ll pay the budget later — in incident hours, SLA breaches, loss of trust, and potentially financial outflows resulting from exactly the manipulated transactions this attack vector enables.
The lesson is not new, but it is more relevant than ever: Public registries are great for speed and reuse, but they are not a trusted part of your production supply chain unless you enforce quarantine, verification, and immutability yourself; those who do not implement this today rely not on resilience but on luck — and luck is not a security strategy.
The security of the software supply chain is one of the central topics in modern software …
Imagine buying a ready-made meal at the supermarket without an ingredient list. For years, this was …
TL;DR GitLab CI/CD is much more than a build tool: When used correctly, it becomes the central …