The Full Coverage Insurance
for Your Software Stack
And how does it work?
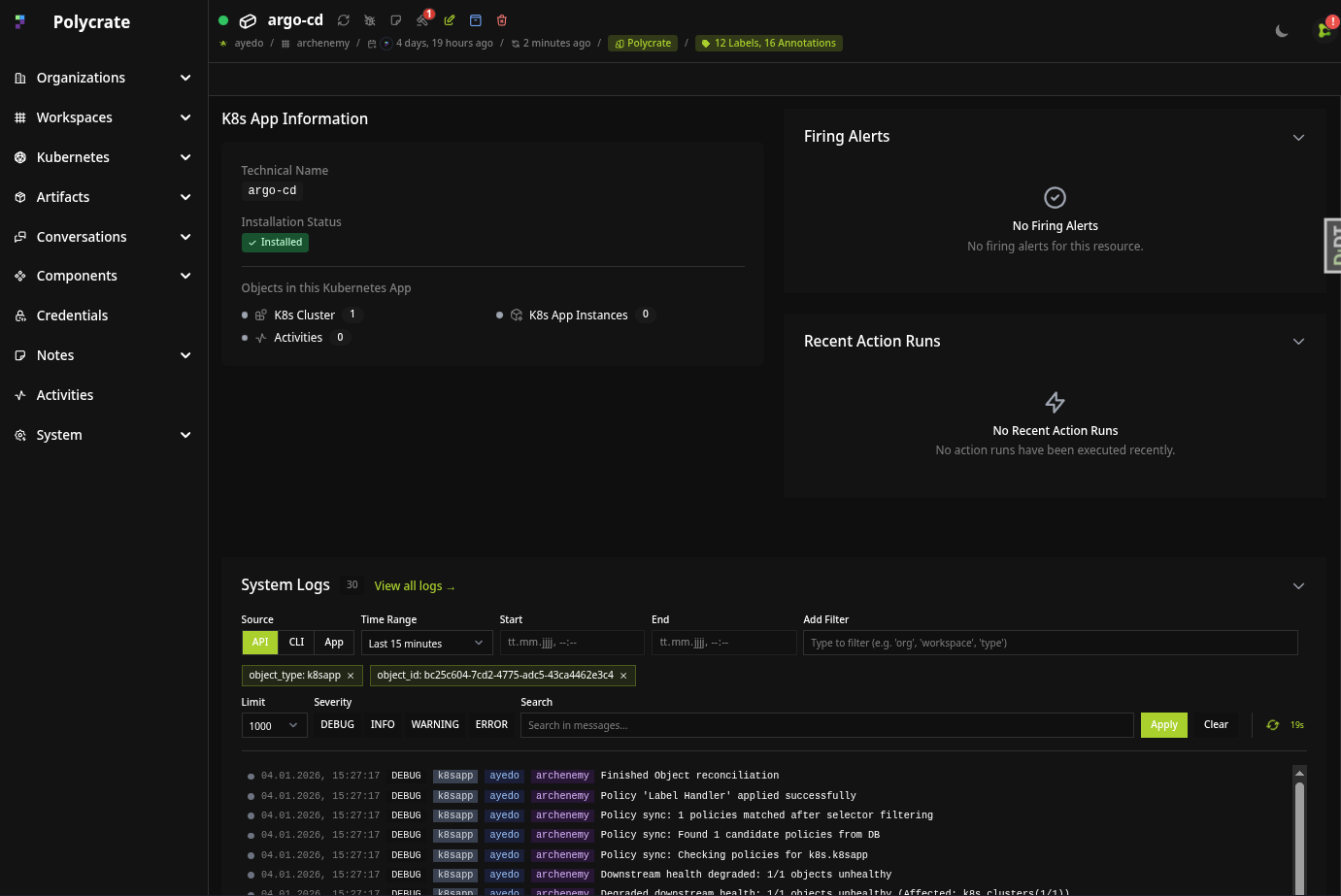
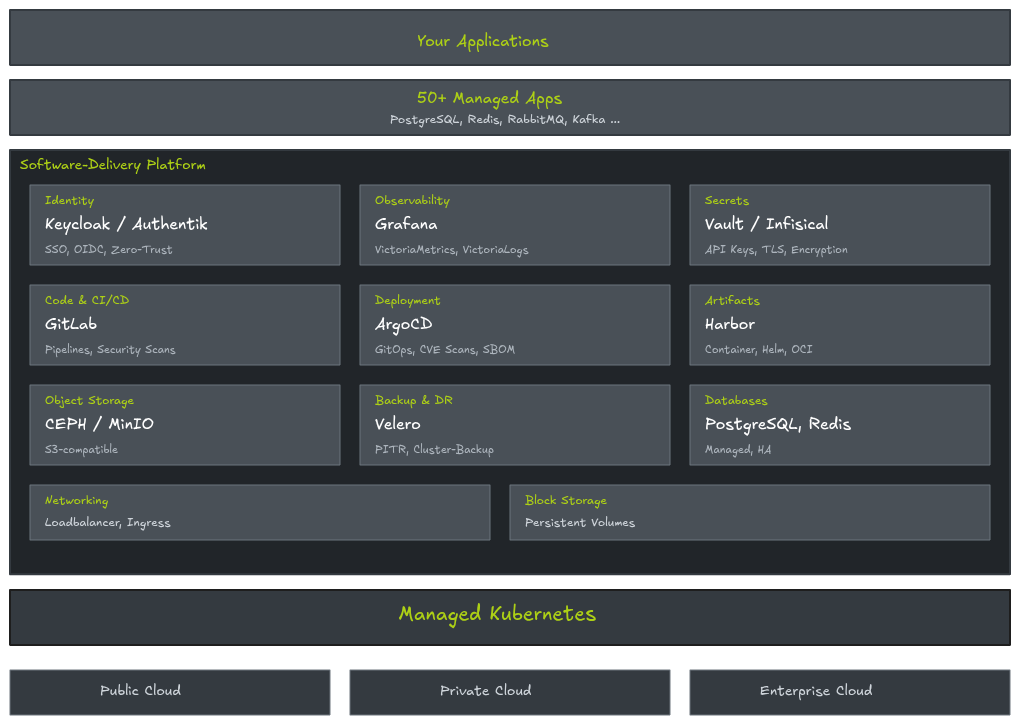
Our Software Delivery Platform is a managed service solution for companies that want their software operations in expert hands and value personal support. You develop, we operate. Unlike other managed service providers, you receive not only pure cluster and app operations, but a service package fully tailored to highly available software delivery and personal support from our platform team.
Monitoring
Support
No software is like another
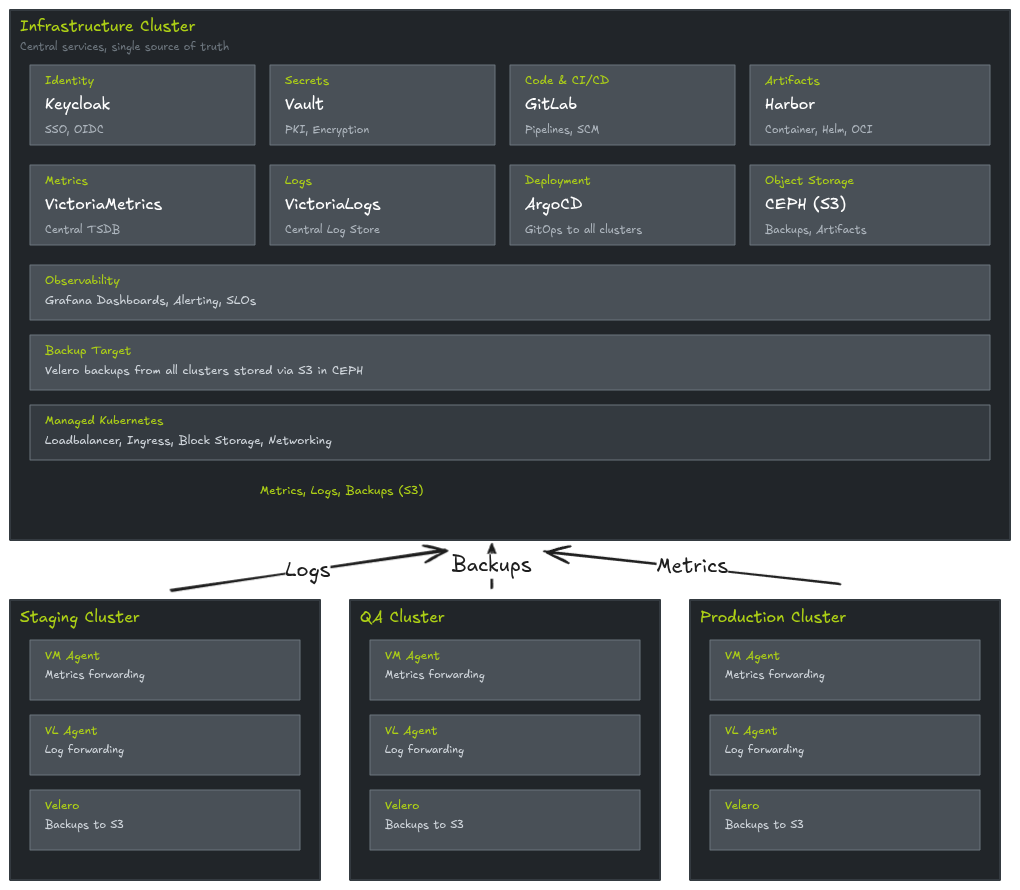
The ayedo Software Delivery Platform is a turnkey platform for running software on Kubernetes. ayedo operates the platform on supported Cloud Providers or on your own On-Premise infrastructure – you retain full control over the location of your data and workloads.
Public Cloud
Private Cloud
On-Premise
You build it. We run it.
Excellent performance and maximum uptime - that’s what we wake up for. And sometimes even in the middle of the night.
270 Million End Users
per month
99.99% Uptime
annual average
MTTD < 5 Minutes
on average
34 Billion Logs
per month
71 Million Active Timeseries
per month
50 TB Backups
per month
Compliance & Regulatory Requirements
The ayedo Software Delivery Platform meets the requirements of current EU regulations. From GDPR to NIS-2 to DORA – our platform is designed for regulated industries and critical infrastructures.
GDPR-Compliant Data Processing
Privacy by Design & Default.
NIS-2-Compliant Operations
Resilience for critical infrastructures.
DORA-Ready for Financial Institutions
ICT resilience tailored.
CRA-Compliant Software Supply Chain
Security by Design across the entire lifecycle.
Cloud Sovereignty Framework
Digital sovereignty made measurable.
Data Act-Compliant Portability
Switching without barriers.
Integrated Compliance Roadmap
Holistic approach.
Features
The ayedo Software Delivery Platform delivers a comprehensive set of platform components for secure, scalable software operations on Kubernetes. Combined with the Polycrate API, additional features like Endpoint Management, Multi-Region Load Balancing, and SLA/SLO Tracking are available.
Identity Management
Monitoring & Alerting
Object Storage
Secrets Management
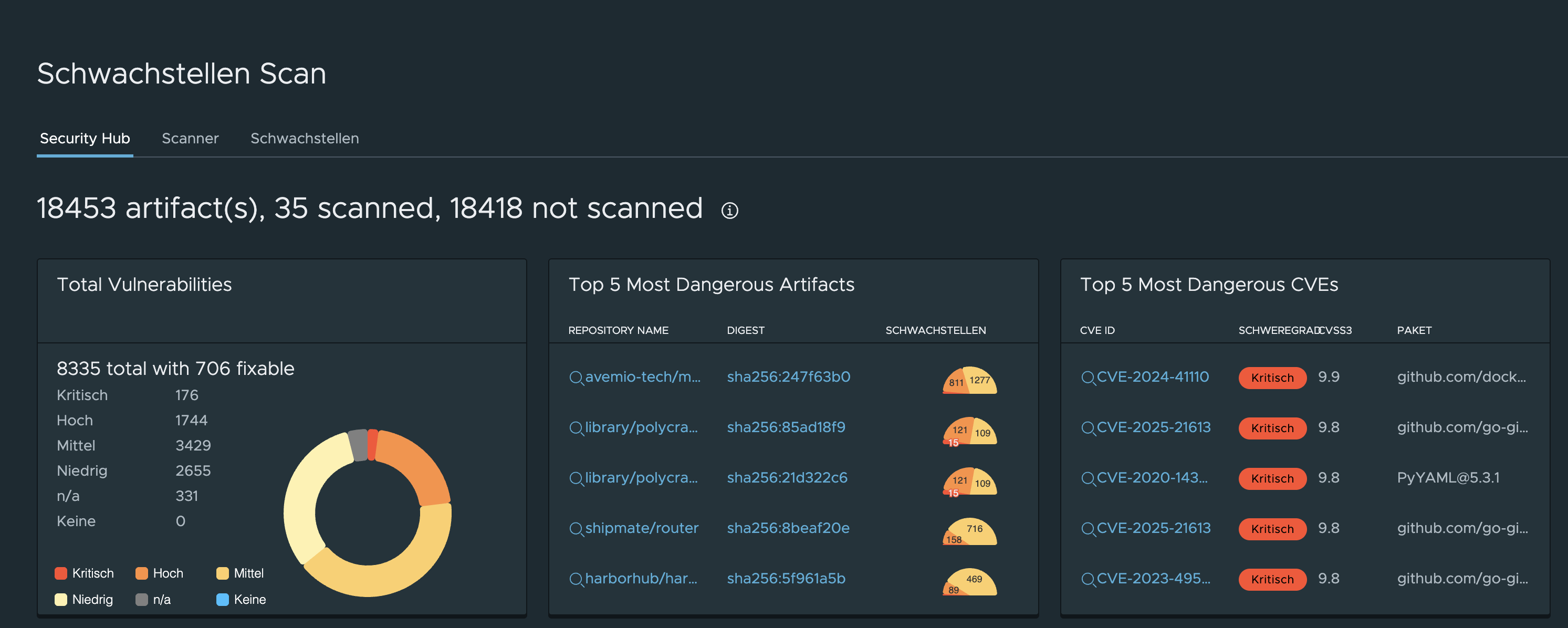
Artifact Management
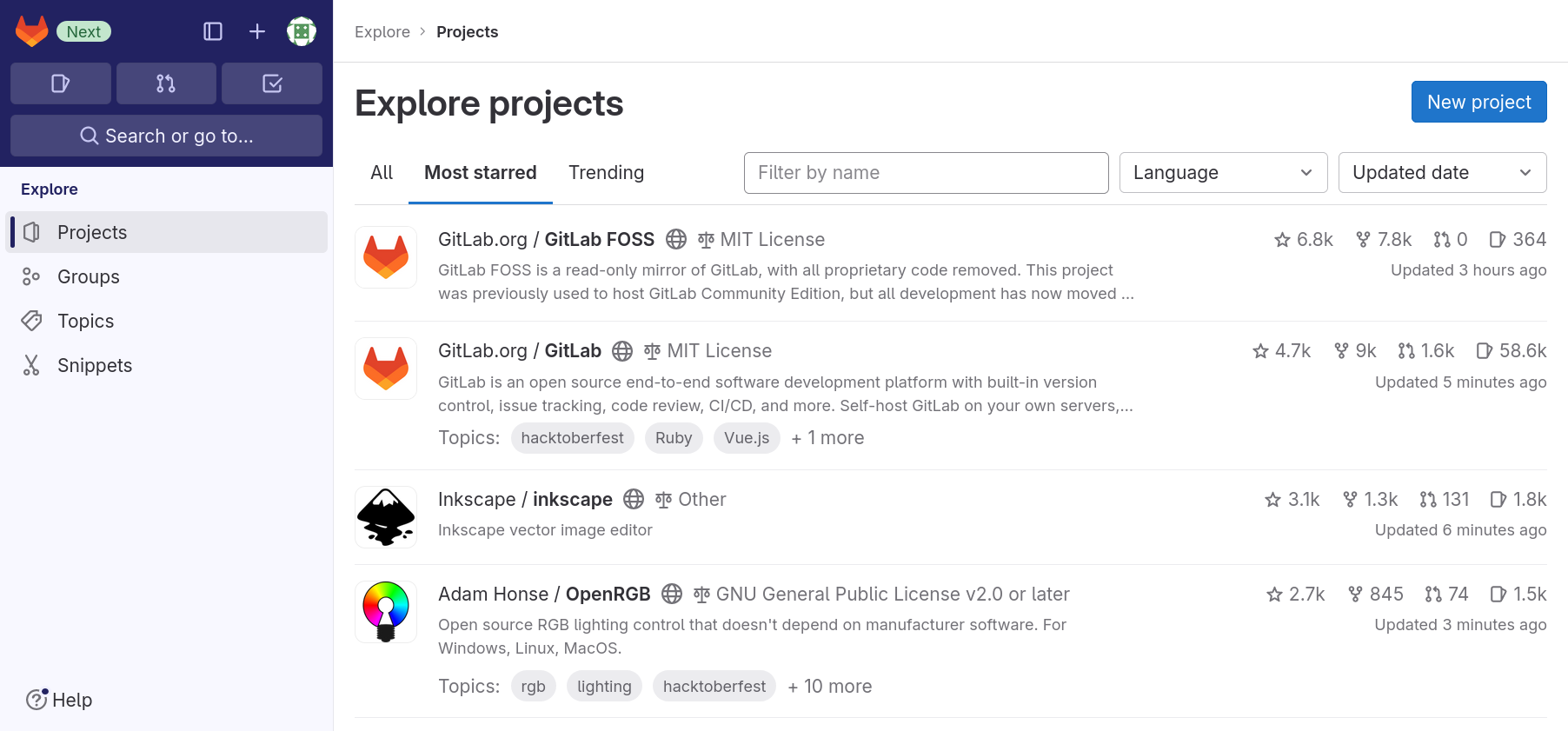
Code Management
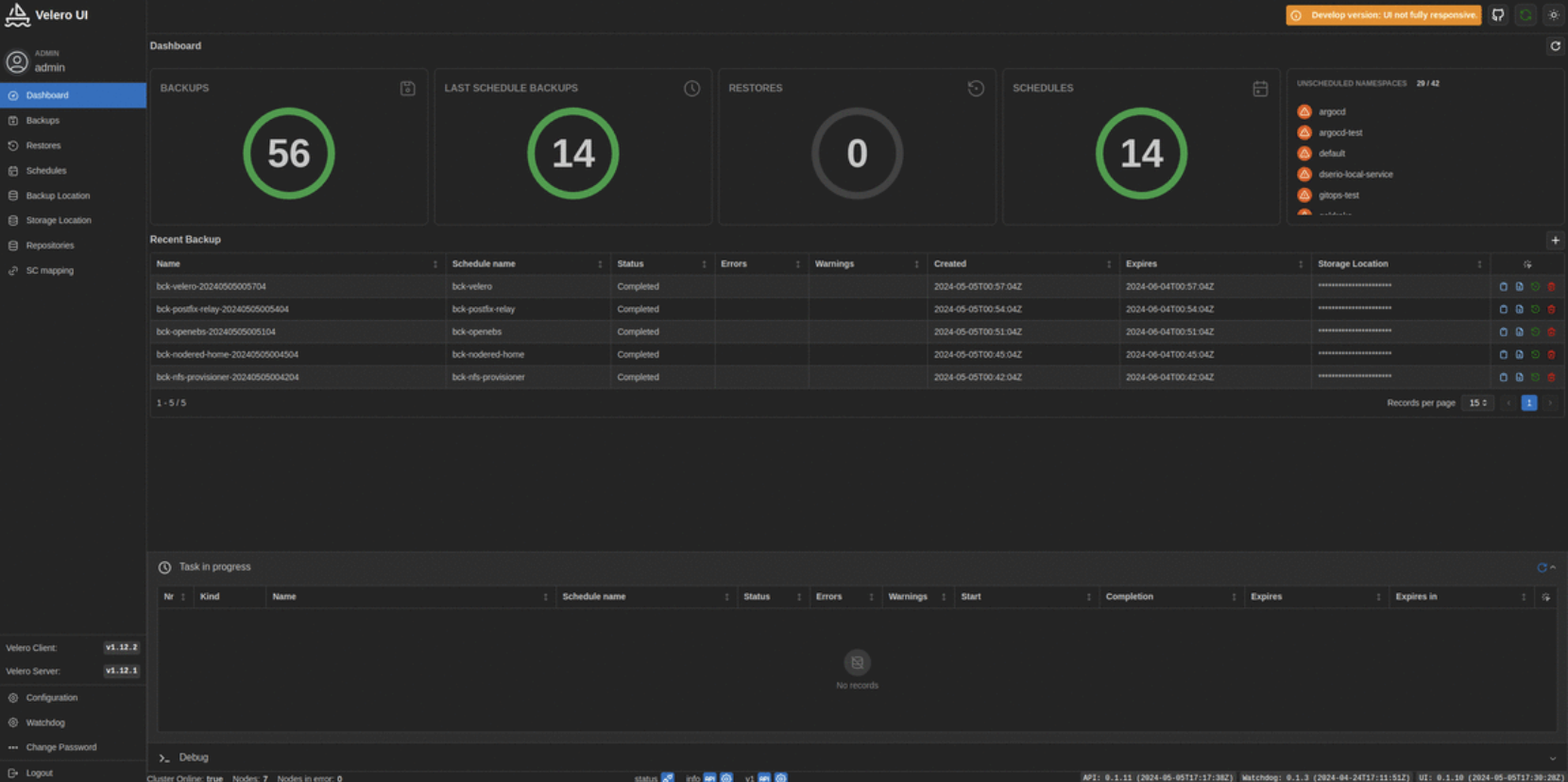
Backup & Restore
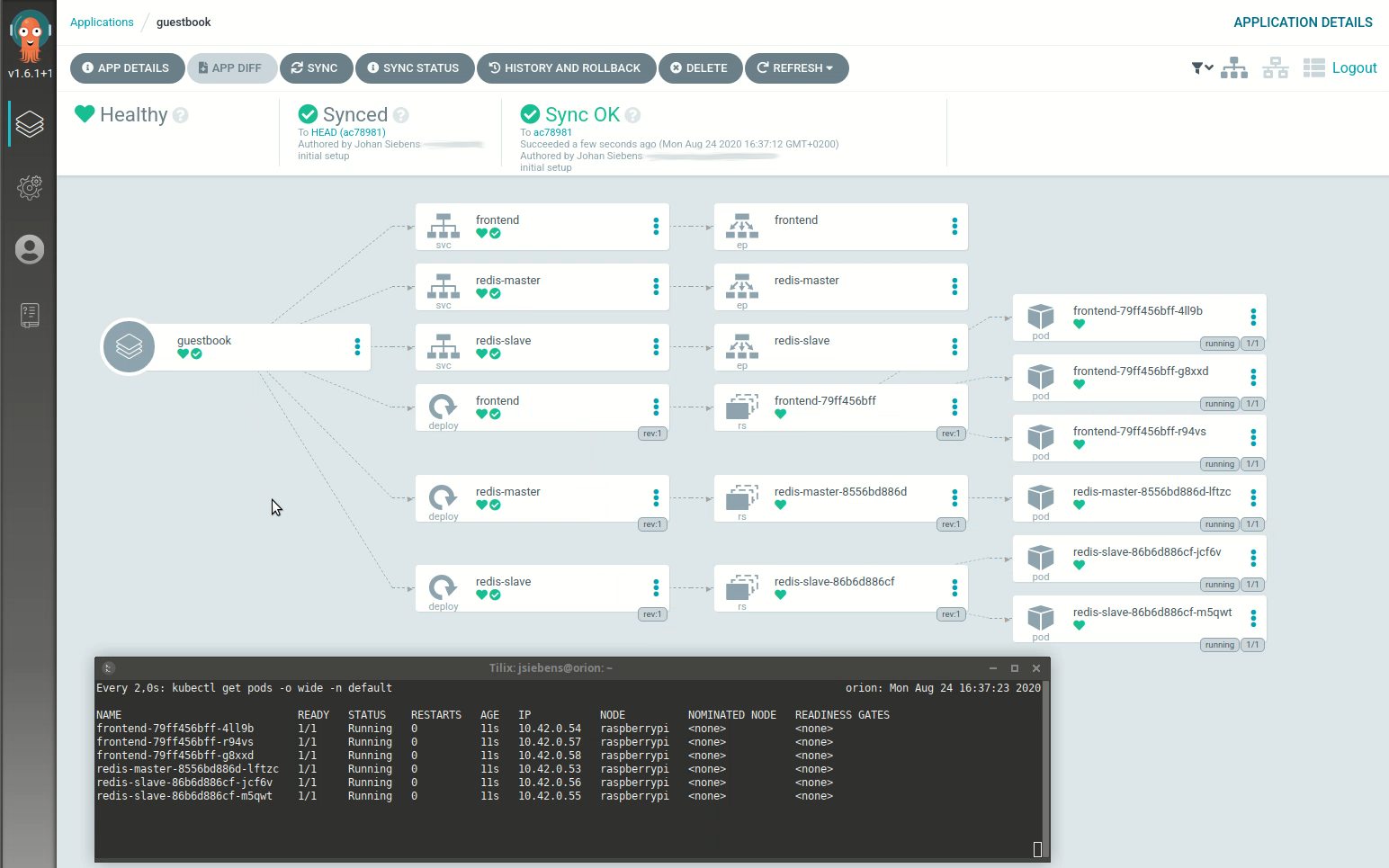
Deployment
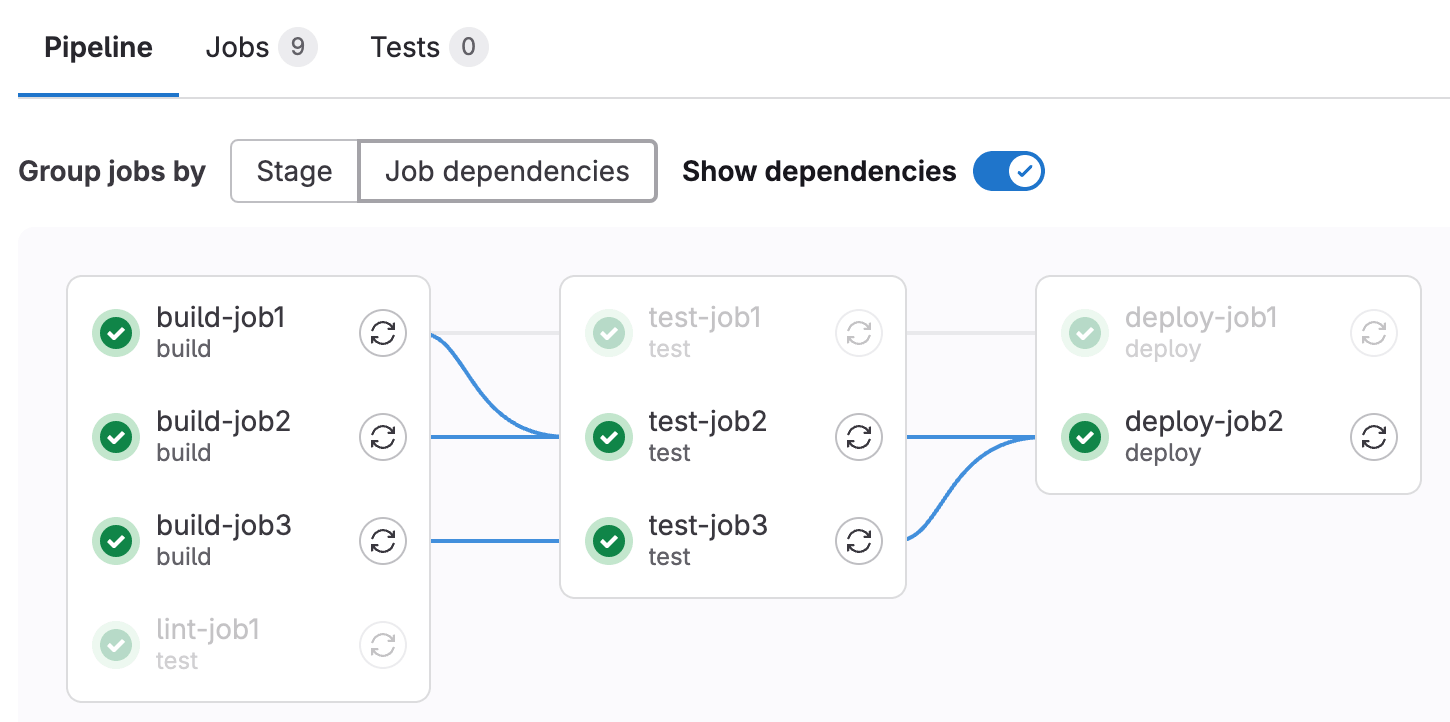
Continuous Integration
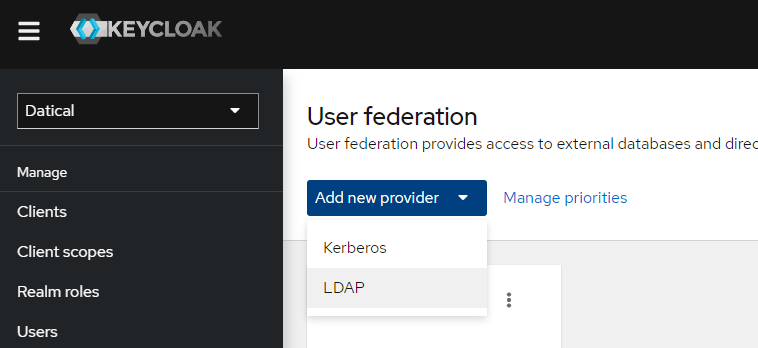
Active Directory Integration
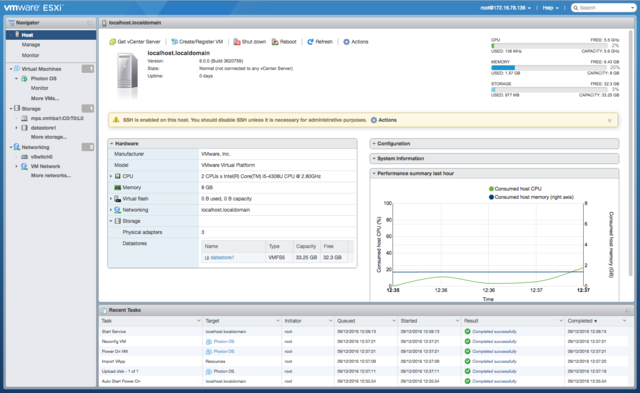
VMware Support

On-Premise Support
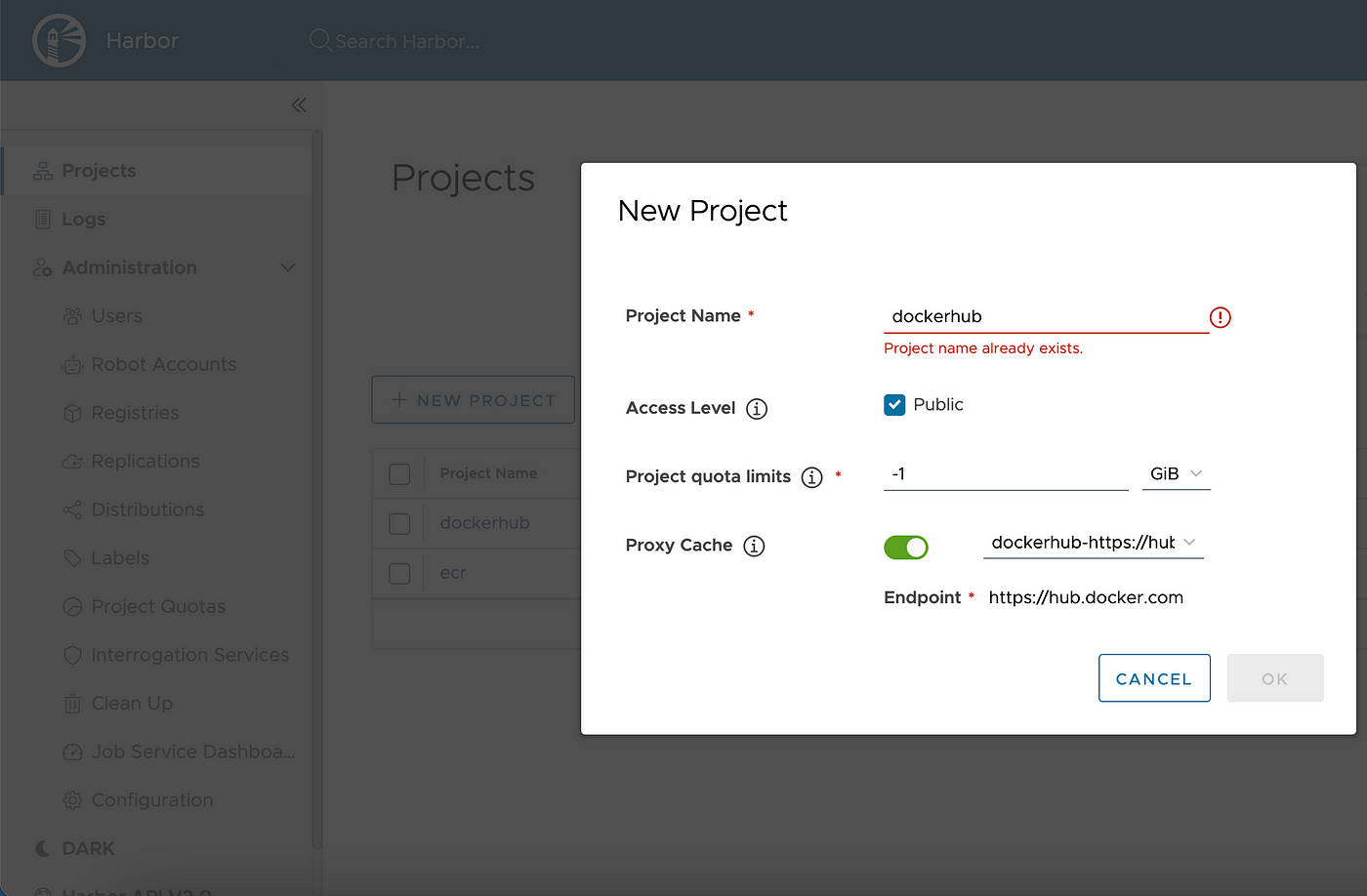
OCI Registry Proxy
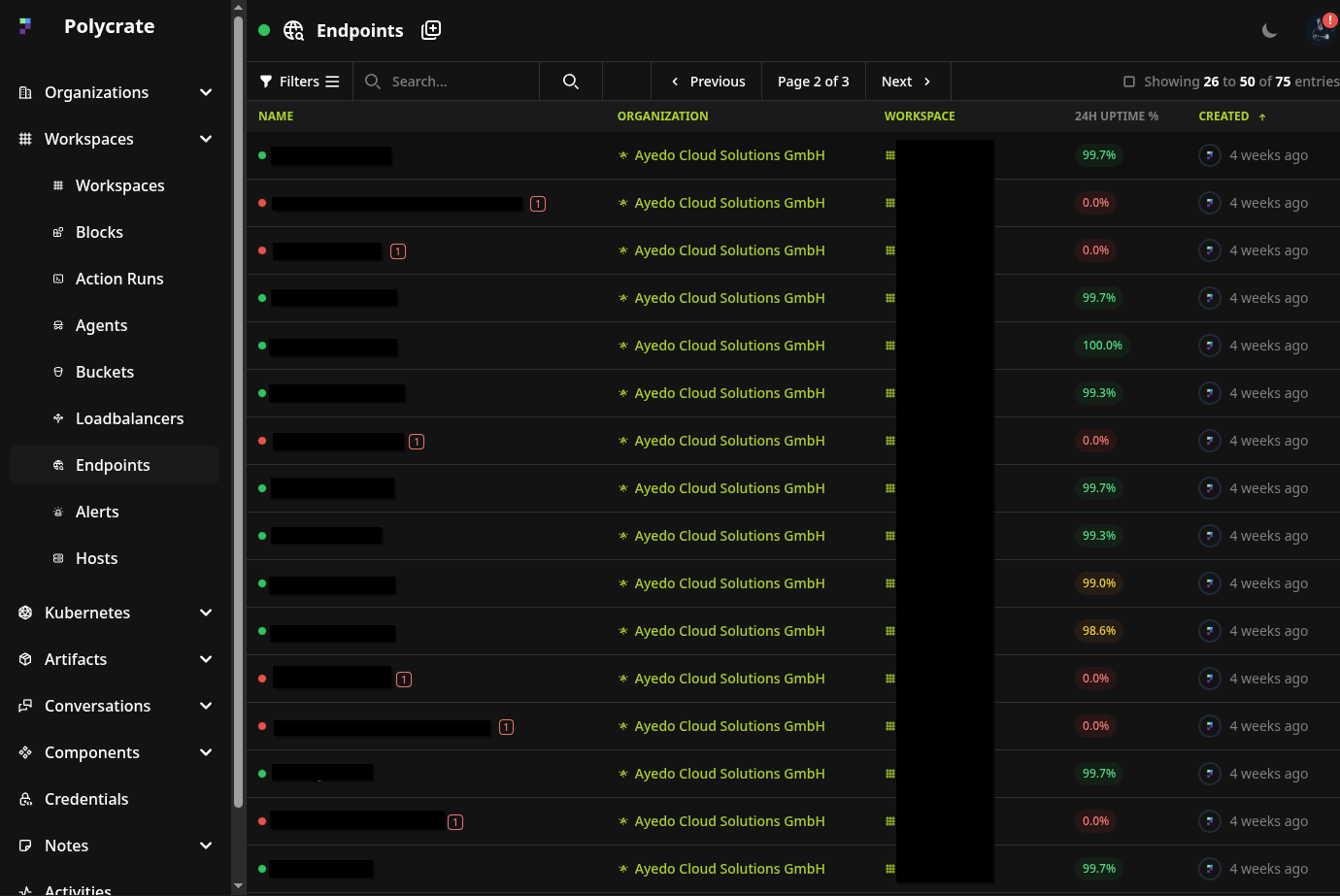
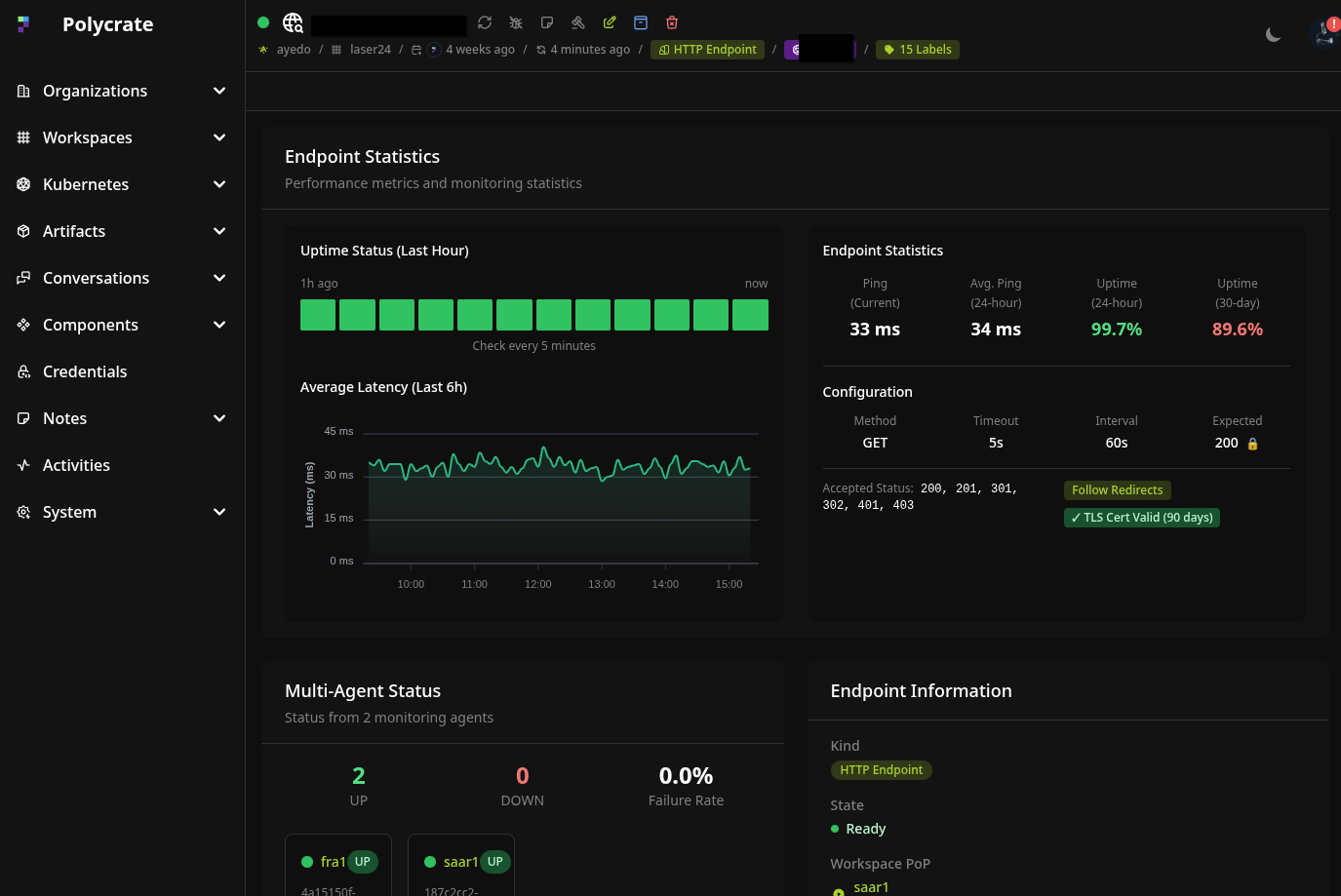
Endpoint Management
Multi-Region Load Balancing

Multi-Region S3 Management