Regulatory Pressure
New laws, stricter requirements
- The EU is harmonizing cybersecurity, data protection and digital sovereignty EU-wide
- National patchworks are being replaced by binding regulations
Digital transformation has created new risks – and the EU is responding with a coherent regulatory framework. Whether financial sector, critical infrastructure or software development: anyone who operates, sells or offers software as SaaS must address these requirements.
New laws, stricter requirements
Security as a competitive advantage
High fines, reputation losses
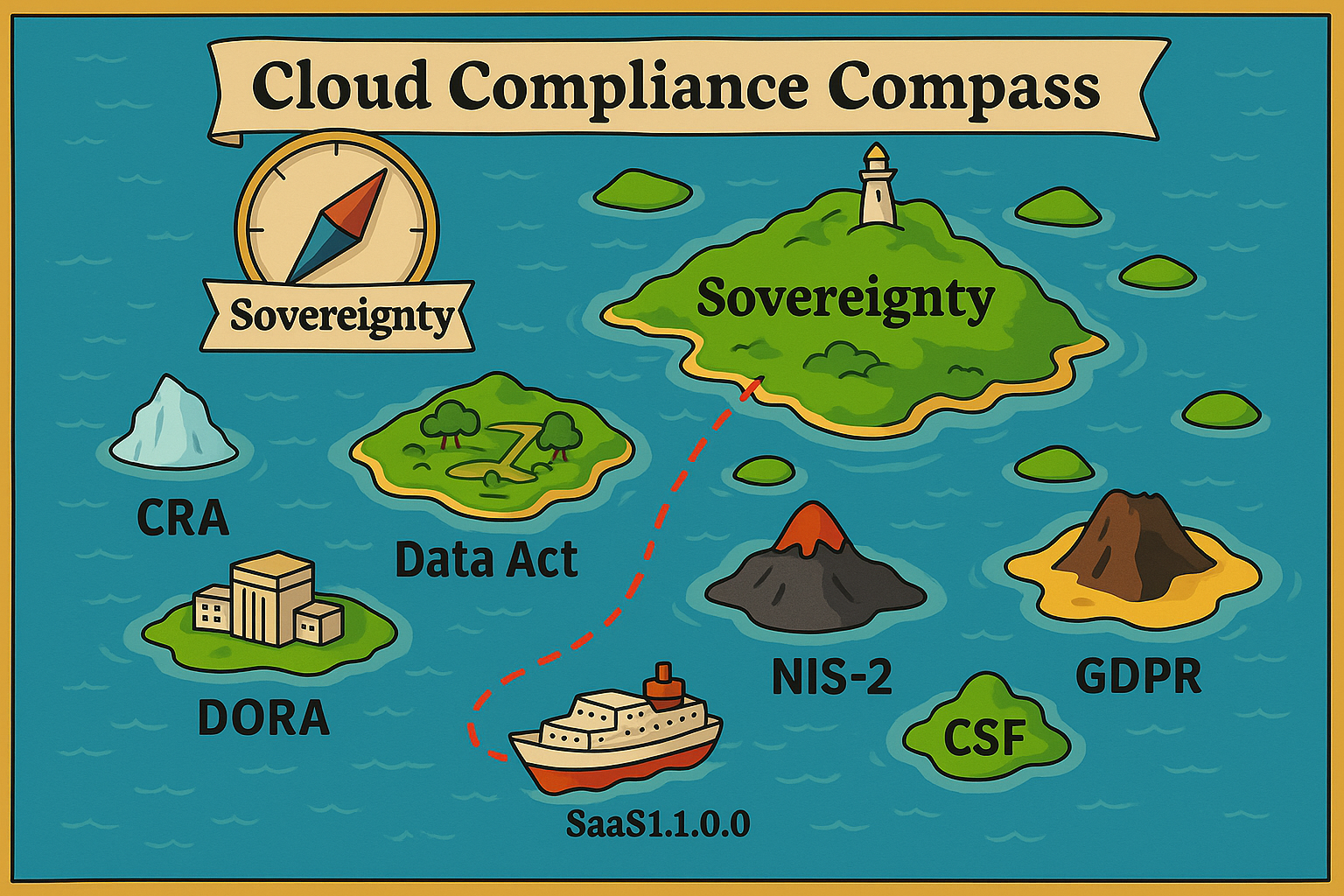
Seven central regulations and frameworks shape the digital compliance landscape. Each addresses specific risks – together they form a coherent ecosystem.
Privacy by Design & Default
In force since 2018. Protection of personal data, data subject rights, notification obligations. Affects every company processing EU citizens’ data. Fines up to 4% of annual turnover.
Cyber resilience for critical infrastructures
Applicable from October 2024. Extends NIS-1 to 18 sectors. Risk management, incident reporting, supply chain security, management liability. Affects essential/important entities.
ICT resilience for the financial sector
Applicable from January 2025. Harmonizes ICT risk management, testing, third-party risk. Affects financial institutions and their ICT service providers. Lex specialis to NIS-2.
Security by Design for products
Applicable from 2027. Product security over entire lifecycle, SBOM, vulnerability disclosure, update obligations. Affects software/hardware manufacturers. CE marking for critical products.
Switching without barriers
Applicable from September 2025. Data portability, open APIs, prevention of vendor lock-in. Affects cloud providers, IoT manufacturers, software vendors. Functional equivalence and exit runbooks mandatory.
Digital sovereignty made measurable
EU Commission procurement framework. Evaluates cloud services against 8 sovereignty objectives (SOV-1 to SOV-8). SEAL levels as minimum thresholds. EU preference in public procurement.
Cloud-Native Done Right
Methodology for modern, portable, scalable SaaS applications. Codebase, Dependencies, Config, Services, Build/Release/Run, Processes, Port-Binding, Concurrency, Disposability, Dev/Prod-Parity, Logs, Admin, Security, Telemetry, API-First.
EU regulations are not an isolated patchwork, but a coherent ecosystem. Many requirements overlap – leveraging synergies is key.
Privacy by Design runs through everything
Cyber resilience for critical infrastructures
Secure, portable products
Sovereignty as selection criterion
Cloud-Native as enabler
Done right once, many goals achieved
EU regulations are not toothless. Violations can result in existential fines, reputation losses and business restrictions.
High fines, reputation losses
Personal responsibility of management
Interventions in business operations
Market surveillance can ban products
Exit rights can be enforced
No public contracts without SEAL
Some regulations are already in force, others follow in the coming years. Early preparation is crucial – retrospective compliance is more expensive.
Act now
18 months implementation period for member states
Financial sector must deliver now
Product manufacturers have time to prepare
Cloud providers and IoT manufacturers: Act now
Procurements are using the framework now
Compliance is complex – but not impossible. ayedo offers you a platform, processes and expertise to systematically address GDPR, NIS-2, DORA, CRA, Data Act and Cloud Sovereignty Framework.
Privacy by Design & Default, out-of-the-box
Resilience for critical infrastructures
ICT resilience tailored to requirements
Security by Design over entire lifecycle
Digital sovereignty made measurable
Switching without barriers
Portable, scalable SaaS applications
We show you the way
One approach, many goals
Compliance doesn’t have to be overwhelming. With the right platform, the right processes and the right partner, regulatory burden becomes competitive advantage.
Let’s analyze your status quo together and develop a roadmap.
See live how our platform addresses GDPR, NIS-2, DORA, CRA, Data Act and Cloud Sovereignty Framework.
Request our detailed compliance dossiers: