Weekly Backlog Week 10/2026
🧠 Editorial: Cloud is political. Period. This issue focuses on a topic often wrapped in technical …


Anyone who still claims this week that security, resilience, or digital sovereignty are mere implementation details hasn’t been paying attention. Or didn’t want to. The topics in this issue have nothing to do with zero-days or “highly complex attacks.” They are about valid credentials, deliberate political decisions, and structural convenience.
The common thread: Control is delegated—to tools, providers, processes, or simply to “later.” And later is surprisingly often exactly when things go wrong.
More than 10,000 publicly available Docker images on Docker Hub contain production credentials. API keys, cloud accesses, database credentials, sometimes with direct access to production systems. This is not an exception, not a rookie mistake, not an unfortunate slip by individual teams. It is the logical result of today’s development and release practices.
The images analyzed by Flare often come from organizations that don’t even know their artifacts are public. Particularly alarming is not just the sheer quantity but the quality of the leaks: 42 percent of the affected images contained multiple secrets simultaneously. This doesn’t mean a compromised service, but entire environments—including cloud accounts, software distribution, and data management.
Notably, the type of secrets that dominate: A large portion involves API keys for AI and LLM services. New platforms, new business models—but old security patterns. Keys are generated, integrated into build processes, passed on, and forgotten. Lifecycles are not technically enforced, responsibilities are diffuse, central control is lacking.
Particularly fatal: In many cases, the credentials were removed from the images later, but never revoked. The keys remained valid. For attackers, this means no break-in, but logging in with functioning credentials. The damage is not caused by sophistication, but by validity.
Docker Hub is just the most visible tip. Comparable leaks can be found in Git repositories, internal registries, CI/CD pipelines. Everywhere secrets become part of artifacts, the loss of control is not an accident but factored in.
Without technical exclusions of secrets, automated checks before releases, and consistent rotation of compromised keys, containers and cloud are not an efficiency gain but a scaled attack surface.
In Bavaria, a framework agreement with Microsoft worth nearly one billion euros over five years is to be concluded—without a tender. No competition, no offer review, no serious evaluation of European alternatives. Computer scientists, representatives of the IT industry, and the open-source community are sounding the alarm, calling it an incalculable strategic risk for the digital capability of the Free State.
The core of the criticism is not ideological but structural: Central administrative IT and sensitive data would be entrusted to a US corporation legally subject to the directives of the US government. Cloud Act, FISA, Executive Orders—all known, all documented. The timing is particularly significant: The new US security strategy explicitly ranks European interests lower.
Even the Bavarian State Office for Information Security warns of geopolitical dependencies and security risks. Without any noticeable effect. Finance Minister Albert Füracker insists on the deal and uses a legal loophole to push through the contract without a tender. European providers are not excluded—they are not even asked.
While federal states like Schleswig-Holstein or Thuringia are building open-source stacks and sovereign cloud structures, Bavaria consciously chooses the easiest path. This decision is not technically motivated. It is political. And it systematically devalues its own IT competence and regional value creation.
It’s good that this debate is now being conducted publicly. It’s bad that it apparently only begins after facts were supposed to be created.
During the visit of Ukrainian President Volodymyr Zelensky, there was a major IT outage in the German Bundestag. Internet access and email traffic were affected, systems were completely shut down and later restarted. Cause unclear, the BSI is investigating.
Whether it was an external attack is still open. However, the disruption had immediate diplomatic consequences: A planned video conference between EU foreign ministers and US negotiators could not take place. The incident occurred amid sensitive talks on Ukraine and international security issues.
Inevitably, memories of the 2015 Bundestag hack are revived, where the parliamentary network was comprehensively compromised. Back then, it took years for the full extent to be politically acknowledged. Today, it is once again evident: Critical IT infrastructure is often only recognized as such when it fails—and precisely when it is needed.
What is regularly deemed unrealistic in Germany has been running productively in France for years: The Ministry of Education provides its employees with cloud storage—without US hyperscalers. The platform apps.education.fr is based on Nextcloud, operated in its own data centers, and offers 100 GB of storage per person.
In use since 2018, scaled within a week during the pandemic, fully transferred to its own data centers after the OVH fire in 2021. Today, over 337,000 employees use the service, with a perspective of reaching 1.2 million. The architecture is complex, federated, integrates existing systems like Tchap or Zimbra, and manages a directory with over a million identities.
Problems exist—naturally. Interesting is the approach to them: Instead of switching to a hyperscaler, the ministry works with the open-source provider on concrete improvements. 150 tickets in 18 months. No illusion of perfection, but controlled development.
This project disproves several narratives: That state IT cannot scale without hyperscalers. That open source is not operable on a large scale. And that digital sovereignty is inevitably slower or more expensive. France shows: It’s a matter of decision, not possibility.
The new Cloudflare report reads technically impressive: plus 19 percent internet traffic, over 95 percent HTTPS, more than half of human-generated web traffic already secured with post-quantum encryption. Yet behind these numbers lies a clear power shift.
That 52 percent of web traffic is quantum-secure encrypted is not the result of political foresight or European coordination. It is the consequence of browser updates by major providers and standard activation at Cloudflare. Security here arises not from democratic governance but from the decisions of a few US companies.
At the same time, automated access is exploding. Googlebot causes over a quarter of verified bot traffic and generates more HTML requests than all AI bots combined. User-action crawling for AI has increased 15-fold. Content is systematically turned into training data—mostly without real bargaining power of the providers.
Even in attacks, the front lines are shifting. DDoS attacks reach new records, NGOs and civil society organizations are at the top of the target list for the first time. Almost half of major internet outages are due to deliberately ordered state shutdowns. Internet governance has long been a power tool.
The report is not a neutral status report. It shows how dependent security, availability, and innovation have become on a few global players—and how little Europe strategically contributes to this.
Nextcloud is a strong open-source alternative to Microsoft 365 and Google Workspace and provides the technical foundations for true digital independence. However, the article by ayedo shows why sovereignty does not automatically arise just because you use Nextcloud. The operating model is crucial: User-based licensing approaches can create new dependencies, while a resource-based operating concept in your own Kubernetes cluster enables control, transparency, and scalability.
Anyone looking to strategically deploy Nextcloud will find a clear assessment here of what really matters in the “how.”
🔗 </posts/nextcloud-souveran-betreiben-warum-das-wie-entscheidend-ist/>
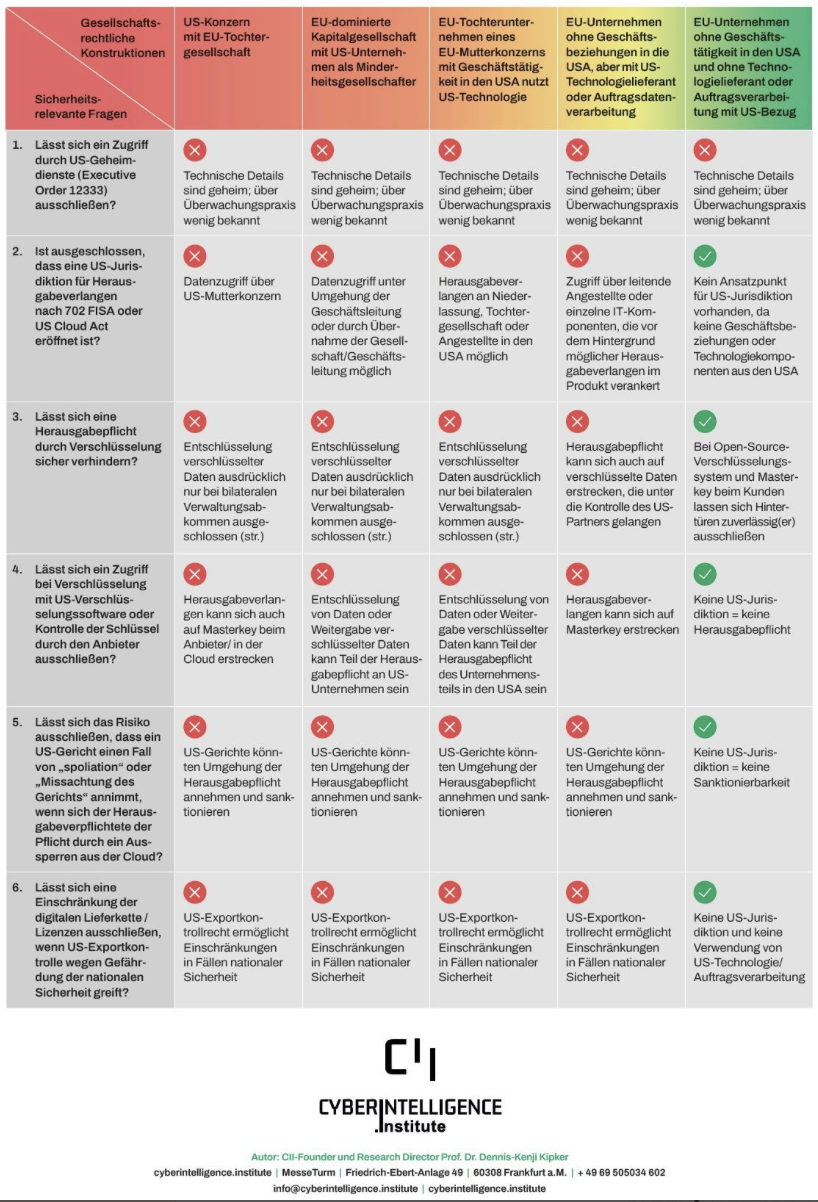
Prof. Dr. Dennis-Kenji Kipker demonstrates with the Cloud Risk Matrix developed by the cyberintelligence institute what is systematically ignored in political debates and marketing slides: Digital sovereignty in the cloud is currently mostly an assertion, not a reliable attribute.
Executive Order 12333, FISA 702, CLOUD Act, export control law, corporate structures, and technical access possibilities are not considered in isolation but in their interaction. The result is clear: The common constructs with which international cloud providers market their offerings as “sovereign” do not withstand a comprehensive examination.
Affected are not only US corporations but also European companies with US ties, US technology in the stack, or US contract processing. Even organizations without direct US relations remain vulnerable as soon as they rely on corresponding supply chains. Contract clauses and data center locations change little about this.
The analysis is a reality check for politics, administration, and companies. As long as Europe bases its digital infrastructure on foreign legal frameworks and proprietary technologies, sovereignty remains a marketing term.
Björn Bergfelder has canceled his subscriptions with Google, Apple, and Netflix and pulled his data from US clouds.
🧠 Editorial: Cloud is political. Period. This issue focuses on a topic often wrapped in technical …
🧠 Editorial: The Week of Sovereignty Simulations This week had it all: operating systems wanting to …
🧠 Editorial If you’ve noticed: The Weekly Backlog looks a bit different. Now even more …