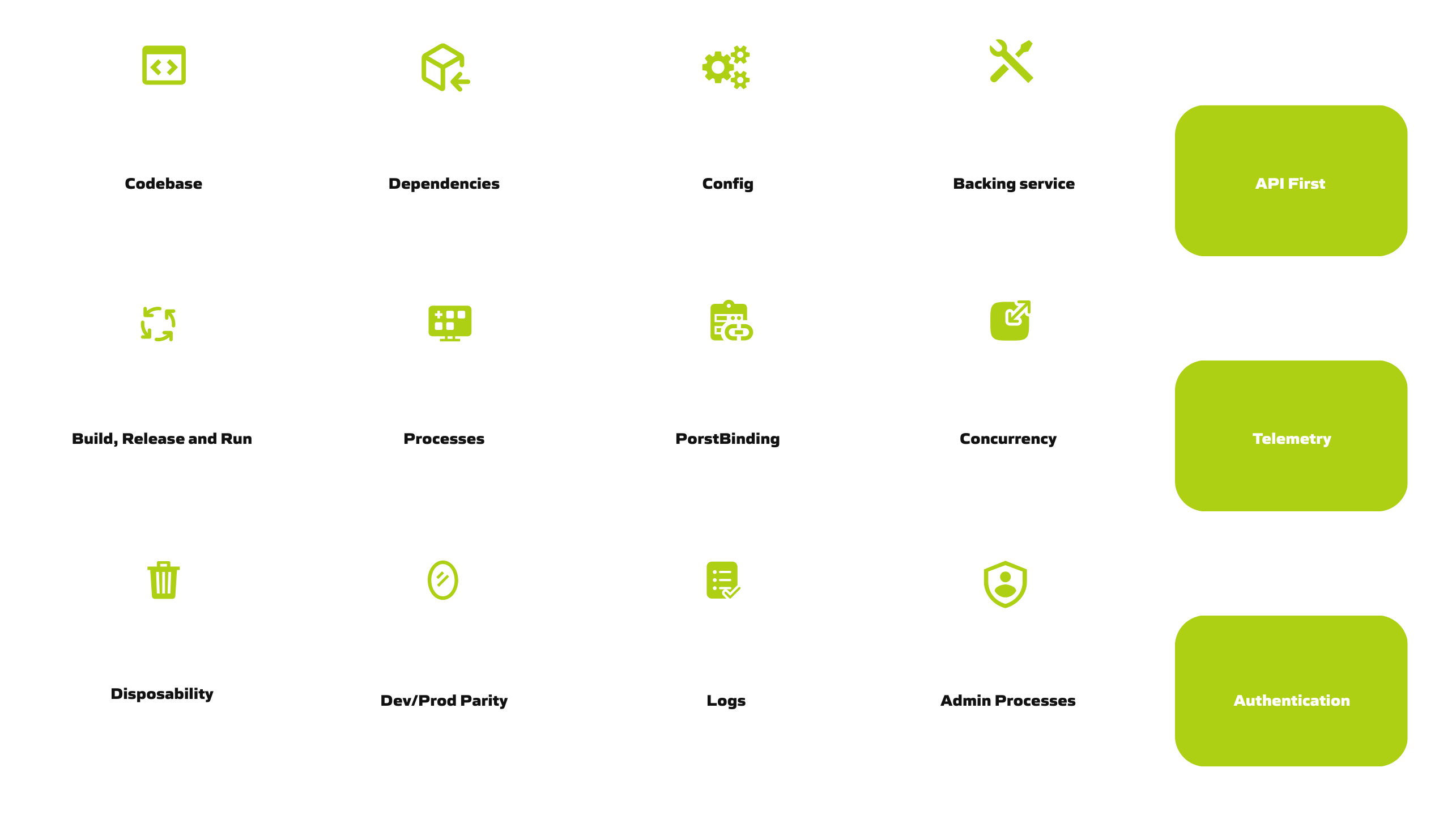
15-Factor App
Principles for Cloud-Native Applications
From 12 to 15 Factors
The original 12-Factor App principles from Heroku were groundbreaking for cloud-native development. With the evolution of cloud infrastructure, microservices and security requirements, three more essential factors were added: API First, Telemetry and Authentication & Authorization.

Factors 1-3: Foundations & Dependencies
The first three factors form the foundation for reproducible and maintainable cloud applications. They define how code is managed, dependencies declared and configuration separated from code.


- Dependencies
requirements.txt, package.json, go.mod). The application must never rely on system-wide packages.
- Config
Factors 4-6: Services & Lifecycle
These factors define how applications interact with external services and how the lifecycle from build to runtime is organized. They promote loose coupling and clear separation of deployment phases.
- Backing Services

- Build, Release, Run
- Processes
Factors 7-9: Networking & Scaling
The factors for modern network architecture and horizontal scaling. They describe how services are exposed, how scaling works and why fast startup times are critical.

- Port Binding
- Concurrency
- Disposability
Factors 10-12: Operations & Maintenance
These factors address daily operations: How does dev/prod stay in sync? How are logs handled? And how do you run administrative tasks without violating the 12-factor principles?
- Dev/Prod Parity
- Logs

- Admin Processes
Factors 13-15: Modern Cloud-Native Extensions
The three new factors reflect the evolution of modern cloud architectures: API-First Design for interoperability, Telemetry for observability and Authentication & Authorization for zero-trust security.
- API First

- Telemetry
- Authentication & Authorization
Why 15 Instead of 12?
The original 12 factors were defined in 2011 – an era before microservices dominance, container orchestration and zero-trust security. The three new factors are not optional, but essential for modern cloud-native applications:
API First is Critical
In a world of microservices and distributed teams, API-first is not a nice-to-have, but a prerequisite for efficient development and loose coupling.
Telemetry is Indispensable
Logs alone are no longer sufficient. Without structured telemetry, it is impossible to debug, optimize or meet SLAs for complex distributed systems.
Security is Mandatory
In times of cloud-native, remote work and API economy, zero-trust security is no longer optional. Authentication & authorization must be part of the architecture from the start.
15-Factor Apps with ayedo
Our Managed Kubernetes platform is specifically designed for 15-factor applications. From automatic TLS certificates to integrated observability to identity & access management – we offer everything modern cloud-native apps need.
GitOps & CI/CD
Integrated Observability
Factor 14 (Telemetry) out-of-the-box: Grafana, VictoriaMetrics, Loki and APM Stack for complete observability of your applications.
Identity & Access Management
Managed Backing Services
Factor 4 (Backing Services) made easy: PostgreSQL, MongoDB, Redis, Kafka and many more – highly available and fully managed.
Flexible Scaling
Factor 9 (Disposability) made easy: With Loopback you deploy into your own cloud operating system based on Kubernetes.